Security Realms
VTScada provides the ability to create security realms (referred to as "user groups" in earlier versions). Realms must exist on a hierarchy under at least one layer of management that is not assigned to any realm. A manager who is part of a realm (A realm manager) can see only the roles and accounts that belong to the realm they belong to. All new accounts and roles created by a realm manager will automatically belong to the same realm. A manager who is a member of a realm cannot change or remove their realm membership.
Realms, intended for large hierarchies, must be administrated by at least one user with account privileges that are not restricted to a realm. If you have only one manager account, DO NOT assign a realm to that account. A user with administrator privileges who has been assigned to a realm will no longer have access to Administrative Settings via the Options button in the drop down menu from the user account in the application or via the Application Configuration menu.
If you disregard this warning, you can recover using the Version Control system.
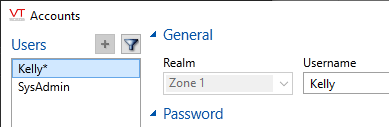
The account, Kelly, is being created by a manager who is a member of realm, Zone 1
There is no choice but to assign Kelly to the same realm.
Why Create Security Realms?
In general, security realms are used by larger organizations with clear separation of duties between groups of users. If using realms, you can expect the following:
- Managers in a realm can access only user accounts and roles in the same realm. Useful for larger organizations with layers of management.
- A manager who is part of a realm can no long access administrator security settings for the application.
- You will be able to use Realm Filtering to restrict user's access to alarm lists and tag lists.
Why Not Create Security Realms?
- The use of security realms requires some extra work during configuration. If creating manager accounts within a realm, it is necessary to populate the realm with it's own roles.
A manager within a realm cannot see the root-level roles unless those have been configured to allow visibility across realms. A manager who is not part of a realm can see all roles and may assign the root-level roles to any account without restriction.
(Roles for one realm should not be assigned to accounts in another realm.) - When security realms have been enabled, Thin Client sign-ins can be done only to an Internet realm matching the user's security realm. Use the RootNamespace property to designate an Internet realm for users who do not belong to any security realm.1
- Both management of ODBC connections and integration with Windows Authentication will require more steps, meaning more chances for mistakes.
You can allow users to set their own filters for tag and alarm lists without defining security realms. Refer to Global Tag & Area Filtering.
When security realms are in use, the sign in process will begin with a prompt for the user's realm before asking for their username (account name). Users who are not a member of a realm can use the tab key or the arrow to step past this.
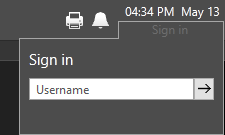
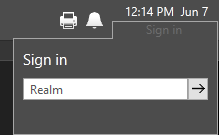
Step 1 of a regular sign in versus a realm sign in.
Security Realms and Realm Filtering
Security Realms are a key part of Realm Filtering, which is a VTScada feature that:
- Restricts the display of alarms to those in areas or tags assigned to the user's realm.
- Restricts the tag browser, limiting the list of tags displayed to those in areas or tags assigned to the user's realm.
- Restricts the selection of tags available for reports to those in areas or tags assigned to the user's realm.
- Restricts the selection of tags available for the Historical Data viewer to those in tag areas assigned to the user's realm.
- Restricts VTScada Thin Client access for the application, forcing users to log into a realm that matches the name of their security realm.
Security Realms are enabled by changing two application properties using the Administrative Settings dialog. (To open, select "Options" within the security menu.) You must have the Administrative privilege and be a root level user(not part of any realm).
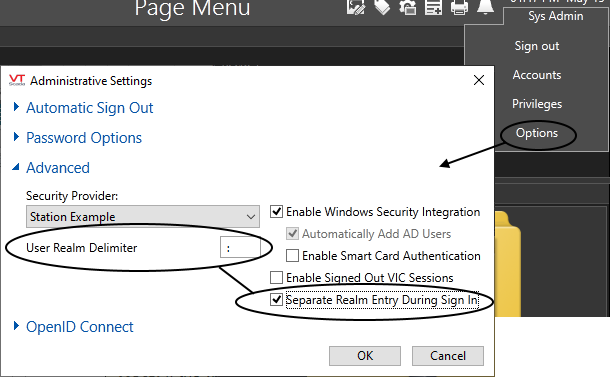
Enabling security realms with the standard delimiter, a semi-colon.
The realm delimiter must be a symbol (neither a letter or a number). While several symbols will work, you are advised to use a colon, which will serve reliably in all situations. You must define the realm delimiter before you can select the option of using separate realm-entry during sign in. Remember that it is necessary to press tab or enter after typing in a VTScada text field.
Do not use characters that could also be part of account names as the NameSpaceDelimiter. For example, a dot is typically part of an account name for any system using Windows Authentication.
While several characters are legal, you are strongly advised to use a colon, which will work dependably in all situations.
Within Settings.Dynamic, these properties are stored as:
- NameSpaceDelimiter= User Realm Delimiter.
- GroupLogin = Separate Realm Entry During Sign In
Create Security Realms & Assign Users to Realms
These two tasks are the same. Realms are created while being assigned to user accounts.
Do not name any realm, "Rest" or "SQLQuery". Doing so will interfere with remote access to VTScada data.
If using Windows Security Integrationand Security Realms, you must add the realm name and prefix to the account using the VTScada accounts dialog. (e.g. realm:username@company.com)
AutoAddADUsers cannot be enabled when a security realm delimiter is defined.
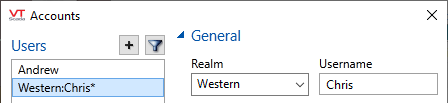
A realm user is one who is associated with a specific security realm. The Realm option is available only after completing the steps described earlier in this topic. (See NameSpaceDelimiter Property above). Realm names are stored as part of the user name, separated by the NameSpaceDelimiter character. (For example, Western:Chris)
When a realm user signs in, they will be prompted for their realm before they can enter their username. Superusers, who do not have a realm, can step past the realm field, leaving it blank.
If signing in with a VTScada Thin Client, users must connect to a realm name that matches their security-realm. You must ensure that the realm is configured in the VTScada Thin Client Server.
Super users, who are not members of any realm, will not be able to sign in via the Internet unless the application property RootNamespace is added, and its value set to the name of a thin client realm created for the use of these accounts.
Visibility of Root-Level Roles With Realms
By default, users within a realm can see only the roles that are also within the same security realm. You can choose to allow roles at the root level (those that are not part of any realm) to be visible (and therefore selectable) within realms. Do so within each role: