Two Factor Authentication for Operators
If your system administrator has enabled two factor authentication with TOTP, the next time you sign in you will be asked to register a device.
Before proceeding you will have to select a device and set up an authenticator![]() A tool or application that verifies the user.. The most common authenticators are applications that can be installed on a mobile device such as a smartphone or tablet. Examples include:
A tool or application that verifies the user.. The most common authenticators are applications that can be installed on a mobile device such as a smartphone or tablet. Examples include:
- Microsoft Authenticator
- Google Authenticator
- Keeper
- Authy
Select an authenticator and install it on your device. For the easiest setup, choose a smart device with a functioning camera.
Have your device ready with the authenticator app open.
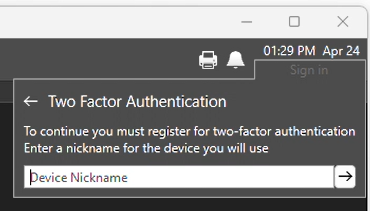
Back in VTScada, give your device a nickname like "Phone" and click the arrow for the next step. Your system administrator will be able to see the device nickname associated with your user account.
A QR code will appear alongside a 32-digit code.
Follow the directions on your authenticator app to scan the QR code.
You will be asked to provide a TOTP passcode from your device. This guarantees that the registration was successful.
If you do not have a functioning camera on your authenticator device, you can enter the 32-digit code manually. However, you have a limited time to do so before the code expires.
Your authenticator is now registered to your account. Every time you sign in, you must provide your password and a passcode from your device.
What to do if you have lost your device
If your device has been lost or no longer works, tell your system administrator right away. They will unregister your device and you will be able to register a new device (or re-register your recovered device) the next time you sign in.
Security best practices for operators
The greatest security risks happen offline. Always be mindful of your actions and surroundings and stick to trusted devices and networks.
- Password protect your smart phone, tablet or any other device or authenticator you opt to use for TOTP.
- Be aware of phishing attempts. Do not open suspicious emails, click suspicious links or download suspicious files on either your device or your workstation. If someone you know sends you a link or a file, check in with them first to make sure it's legitimate.
- Keep your passcodes and QR codes obscured from line-of-sight just like you would an ATM or debit keypad.
- If you hear from your system administrator that the company has implemented two factor authentication with TOTP, register your device as soon as possible. Don't leave your account unregistered.
