Email Configuration for Alarms and Reports
You will need access to an email server for the following two features of VTScada:
- Sending alarm notifications by email (or SMS-text ready email). Requires a license that includes the VTScada Alarm Notification System.
- Sending reports by email.
In both cases, configuration of the email server is done using the Alarms tab of the Basic mode of the Edit Properties page in the Application Configuration dialog. Outgoing emails use the SMTP protocol. Incoming use the POP3 protocol. You have a choice of authentication methods and can use OAuth 2.0 if required by your email provider.
Before configuring the connection to your email server you must gather information about that server. The following illustrations and figures provide guidance. If using OAuth 2.0, refer to the topic, OAuth 2.0 Protocol.
Outgoing Email Configuration
Used for both alarm notification and reports by email.
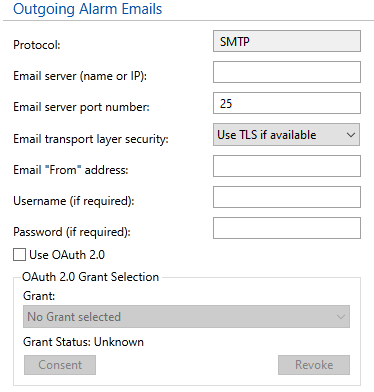
Outgoing Email. This section follows many other alarm configuration options.
These properties are stored in an encrypted format, and cannot be modified in the Settings.Dynamic file.
Customers using basic authentication (username and password) with either Microsoft or Google email accounts must start using OAuth 2.0 or switch to another email provider. For Google, the change-over date was May 30, 2022. For Microsoft accounts, the change-over is scheduled began in October 2022. Refer to Google & Microsoft vs Basic Authentication
| Protocol | Only SMTP is allowed. |
|
Email server name or IP |
The name or IP address of your email server. |
| Email server port number | The port number used by your email server. Always check with your provider to determine the port to use, but for most local email server programs, this will be 25. If using Transport Layer Security, the port will usually be 587. |
| Email transport layer security | Controls whether TLS is used for communications. This is required by most email servers. |
| Email from address | The text you fill in here will be used in the FROM: field of all emails sent by the system. Note that some email servers will check that this is a valid email address and will reject the message if it is not.
If you are configuring for alarm acknowledgment by email, this field must include the email address configured in the Incoming Alarm Email Acknowledgments section. The field may also contain a common name as well as the address. For example: "VTScada System" <VTSSystem@YourCompany.com> Multiple addresses may be used, separated by semi-colons. In the case of alarm acknowledgment by email, the other addresses will be each receive a copy of the acknowledgment. |
| User name |
The account name on your SMTP server, if it is using username / password authentication. Disabled if you are using OAuth2 authorization |
| Password | The password for the account if using username / password authentication. If using Microsoft or Google and not using OAuth 2.0 then you are advised to obtain an App Password as described in Google & Microsoft vs Basic Authentication Disabled if you are using OAuth2 authorization. Both the user name and the password are encrypted for storage. |
| Use OAuth 2.0 | Disables both User name and Passwords fields. Enables access to the OAuth 2.0 configuration dialogs in the VTScada security system. See: OAuth 2.0 Protocol |
| Grant | Select which OAuth 2.0 grant should be used if more than one has been configured. |
| Consent | Initiate the consent process for the selected grant in order to use that email service. |
| Revoke | Revoke consent for the selected grant, ending the ability to use the email account configured with that service. |
Incoming Email Configuration
Used only for acknowledging alarms that were sent by email.
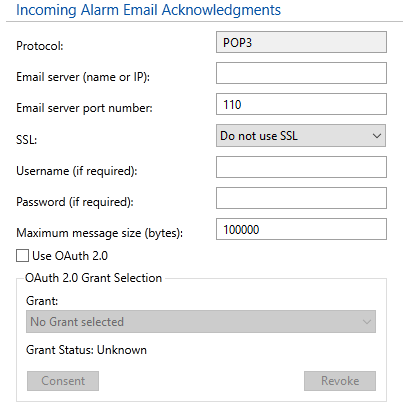
Incoming email configuration. Follows Outgoing Alarm Email Configuration in the configuration properties dialog.
These properties are stored in an encrypted format, and cannot be modified in the Settings.Dynamic file.
Note that the "ack" code in outgoing emails is controlled by the presence of a contact user name in the Roster, not by whether incoming email acknowledgments are enabled.
Customers using basic authentication (username and password) with either Microsoft or Google email accounts must start using OAuth 2.0 or switch to another email provider. For Google, the change-over date was May 30, 2022. For Microsoft accounts, the change-over is scheduled began in October 2022. Refer to Google & Microsoft vs Basic Authentication
| Protocol | Only POP3 is allowed. |
| Email server name or IP | The name or IP address of your email server. This information should be available from your system administrator or your email provider. It will typically take the form: "pop.yourcompany.com" for an internal email server or (using Google’s Gmail as an example) "pop.gmail.com". |
| Email server port number | The port number used by your email server. Always check with your provider to determine the port to use, but for most local email server programs, this will be 110. If using Transport Layer Security, the port will usually be 995 |
| Email transport layer security | Controls whether security is used for communications. This is required by some email servers, such as Google’s Gmail. |
| User name | Use if your POP3 email server requires username / password authentication. Disabled if you are using OAuth2 authorization. |
| Password | The password for your POP3 server account, if it is using username / password authentication. If using Microsoft or Google and not using OAuth 2.0 then you are advised to obtain an App Password as described in Google & Microsoft vs Basic Authentication Disabled if you are using OAuth2 authorization. Both the user name and the password are encrypted for storage. |
| Maximum message size in bytes | Reject any message larger than this size. Use this field to block emails with large attachments, which might otherwise delay legitimate alarm acknowledgments. |
| Use OAuth 2.0 | Disables both User name and Passwords fields. Enables access to the OAuth 2.0 configuration dialogs in the VTScada security system. See: OAuth 2.0 Protocol |
| Grant | Select which OAuth 2.0 grant should be used if more than one has been configured. |
| Consent | Initiate the consent process for the selected grant in order to use that email service. |
| Revoke | Revoke consent for the selected grant, ending the ability to use the email account configured with that service. |
