Two Factor Authentication with TOTP
What is Two-Factor Authentication with TOTP![]() Time-based One-Time Password and Who is it for?
Time-based One-Time Password and Who is it for?
Authentication is the process of verifying that users are who they claim to be. If you signed in to your computer today using a password, that was an example of single-factor authentication. An authentication factor is:
- Something you know (e.g. a password)
- Something you have (e.g. a key fob)
- Something you are (e.g. a fingerprint)
Two-factor authentication with TOTP demands two factors from a user to prove who they are and gain access to a secured account. One of those factors is a password, and the other is a TOTP code provided by something you have, a registered device.
Once two factor authentication is enabled and a device is registered, the user has to provide both of these authentication factors with every sign-in.
TOTP does not need the Internet to work. When a device is registered, your application and the device will share a secret. This tidbit of information and the current time are combined and hashed to produce a secure, unique, and time sensitive passcode. The device and the machine will generate coordinated passcodes because they both know the secret and the time. This makes TOTP especially well-suited for air-gapped systems or systems in places with an irregular connection.
Two factor authentication with TOTP is easy and inexpensive to implement. Once it has been implemented nearly every user account should be using it with very few exceptions. Two factor authentication with TOTP is for everyone except for a single break-glass account.
The few exceptions for exempt users and workstations
You have the final say on exemptions. But the more exemptions that are made, the weaker your security will be.
The break-glass account
Resist the urge to exempt the system admin or super user. Create an account just for this purpose. Exempt only this account. Make sure to use a high-security password and write it down on a slip of paper in a sealed and signed envelope. Keep the envelope in the office in a place where a limited number of people know to look. In the event that the application must be accessed by an account without TOTP, someone will have to retrieve and open the envelope, and then sign in (which is recorded as an timestamped event). The one-time use envelope acts as a substitute authentication factor. It is an alternative to TOTP without sacrificing security.
Users accounts that don't use the user interface
For example, accounts that only use REST API queries or the VTScada Excel Add In. When TOTP is enabled, the Excel Add In works only for exempted users. It is recommended that only remote data access is granted for such user accounts to prevent sign ins or control by less secure accounts. As a general principle, grant no privileges that are not absolutely necessary. General purpose accounts are dangerous.
Workstations that already have MFA
If users must provide multiple factors of authentication to even physically access a workstation (eg. A security check or a key fob to enter the building...), TOTP may be considered redundant.
Special consideration for script-only apps accessed by thin-client
TOTP registration is not supported during thin client sign-in when signing into a script app (eg Application Manager, Source Debugger, etc...).
If you are running VTScada as a service and want to enable TOTP for the Application Manager accounts, you will need to configure it from the Accounts screen.
It is imperative that you register a device for your account (or exempt your account) before signing out from the Application Manager. Otherwise, you will be locked out unless you stop your service and run VTScada interactively.
Configuring two factor with TOTP on your application
To configure TOTP on your application the first step is to enable it for all users.
Enable TOTP in the Administrative Settings dialog. Here, you have the option to reconfigure the time tolerance window, create workstation exemptions or select the label that will be registered in the authenticator. You can find this menu by clicking on your username in the title bar and selecting "Options" (Assuming you have the privileges required.)

This is the menu you can expect to find (You may have to expand the section):
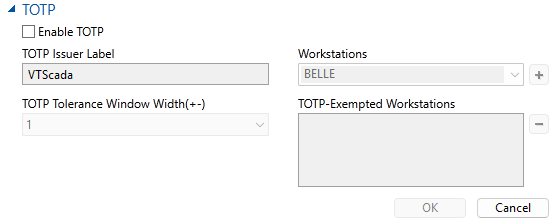
Check the box next to Enable TOTP.
The next time all users sign in, they will be prompted to provide their password and then prompted to register a device. See Two Factor Authentication for Operators for more information on what will be asked of operators. You have the option to access each user account from the Accounts settings to register a device on their behalf or configure user exemptions.
It is a best practice to always have one account that is exempt from TOTP. Ideally this is the emergency bypass "break-glass" account. Credentials for that account should be kept in a secure location and not used otherwise.
Advanced Configuration Settings for TOTP
TOTP Issuer Label
This is the label that will appear in an authenticator.
TOTP Tolerance Window Width (+-)
The number of time periods out-of-sync that can be accepted as a passcode. For example, a width of 1 means we accept the current code, the previous code (-1) and the next code (+1). The minimum setting is 1 to allow for some clock sync tolerance and the natural delay from seeing and typing out the code. The maximum acceptable tolerance is 3 (This would accept the current code, 3 codes before (-3) and 3 codes after (+3).)
The lowest tolerance possible is the most secure configuration. Clock synchronization issues should be resolved instead of weakening the system to accommodate them.
Workstations
To exempt a workstation you must enter the workstation's name exactly how it appears under Workstation Name in the information panel of the application configuration dialog (for that workstation). It also appears in the workstation's PlatformInfo file. Add the workstation by filling in the name and clicking [+].
TOTP-Exempted Workstations
A list of all workstations that have been exempted from TOTP. Remove workstations by clicking to highlight and then clicking the [ - ] button.
If you exempt a thin client server, all thin client connections to that server are exempt from TOTP authentication.
Registering or Removing Devices as a System Administrator
You can register a device on behalf of a user (You will need the physical device in hand). Click on your username in the title bar and go to the Accounts menu. Find the account under "Users" and click on it. Under the section "Multi-Factor Authentication" you will find a box labeled "Devices" with [+][ - ] buttons. Click the [+] button to begin the process.
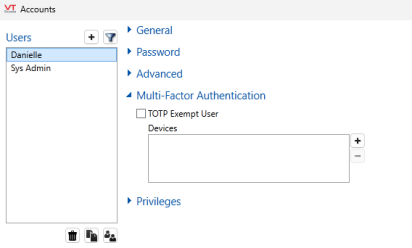
The other sections have been collapsed for the sake of clarity
Just like a typical TOTP registration process, you will be prompted for a Device Nickname and then presented with a QR code to scan with the device. After the code is scanned, you must type in a code from the device. This guarantees that the device has successfully registered the secret.
To remove a device, click on the device in the "Devices" list and then click the [ - ] button.
If a device is reported missing or stolen, remove it from the user account immediately. Encourage users ahead of time to swiftly report stolen or lost devices. Should the device be recovered, it can always be re-added later. Removing a compromised device as an authenticator is just as pragmatic as having the locks changed if the keys go missing and yet much easier, reversible and an inexpensive security measure.
Syncing Clocks
TOTP uses a shared secret and the current time to coordinate the generation of secure passcodes. This requires clocks on both the VTScada system and the user's authenticator to be closely aligned within a tolerance of seconds. Machine clocks, if not externally controlled, can drift considerably. In an Active Directory system, machines usually take their time from the domain controllers (DCs). It is paramount that the DCs get their time from a reliable source.
For air-gapped systems with no access to an external time source, use of a GPS-controlled network time server will be required. This solution is relatively inexpensive.
Security Best Practices
TOTP has some inherent weaknesses. It is important to be aware and to plan and enforce counter-measures to keep your system secured.
- Consider communication vulnerabilities in all of the devices used in TOTP. Use TLS 1.2 or 1.3 for all communication.
- Encourage secure practices for devices used to retrieve an OTP. Phones should be password protected, and users must be educated about phishing attacks.
- Be mindful of shoulder-surfing when the passcode and QR code are displayed. Just like at the ATM, keep secure information shielded from line-of-sight.
- Complete registrations quickly to avoid long-standing unregistered accounts.
- Have as few exemptions as possible.
How to create exemptions for specific accounts
There are a few rare reasons to exempt an account from two factor TOTP. The more exempt accounts you have, the less security you have. It is a Worst Practice to exempt administrators or super users. TOTP will work for users or workstations with unreliable or no access to the internet.
To exempt an account, go to the Accounts menu. Find the account under "Users" and click on it. Under the section "Multi-Factor Authentication" you will find a check box labeled "TOTP Exempt User". Check to enable and exempt the user. Don't forget to apply the changes.
