OPC UA Client Driver
Not counted towards your tag license limit.
OPC UA is an alternative communication protocol to OPC CLASSIC, which used DCOM for communication between a client and a server. VTScada still supports the existing OPC CLASSIC driver.
Unlike OPC CLASSIC, OPC UA, does not rely on third-party "OPC-tunnellers" to act as proxies between the client and server. An OPC UA server may run on a remote computer or be embedded in a smart device and can run on a variety of operating systems. Because there are a limited number of OPC UA products, a tunneller can be used to connect OPC UA clients to an OPC CLASSIC server.
Do not proceed with OPC UA Client Driver configuration until you have read the related information in the topic, OPC UA Support & Security
If both client and server are using OPC UA, the only additional configuration necessary is to ensure that firewalls allow the correct ports to be opened and that trust is established between the server and client. The port(s) in use are defined by the OPC UA server.
The "None" security policy permits communication without encryption or message signing (no confidentiality or integrity). This should only be selected for testing or when the connection is otherwise protected by external means, such as a VPN between the VTScada system and the OPC UA server.
Where encryption or cryptographic signing of communication is desired (recommended), a trusted certificate is required at both the OPC UA server and the VTScada OPC UA Client driver to verify identity.
Unlike many other drivers, the OPC UA Client does not use a Port tag to communicate with its device (OPC UA server). Due to the nature of the binary protocol, the OPC UA Client has port handling built-in.
If VTScada and the UA server are out of time synchronization by more than 5 minutes, the connection will not be made. The driver will return a 520 error, indicating a large time differential.
The OPC UA Client Driver Statistics Dialog widget provides an "Endpoints" button, which when pressed, will display the list of OPC UA Server Endpoint information that is retrieved by the driver and held internally. This information may be helpful when trying to diagnose connection issues or user authentication problems.
Importing tags from an OPC UA device
Not all OPCUA nodes are considered to be tags and therefore not all can be imported. The Tag Browser's Import tool will place properties of tags inside the I/O tag where possible instead of bringing them in as separate IO tags.
If the latter functionality is desired, the user will have to create their own independent I/O tags for this purpose.
Certificate Grids and Controls
Several tabs in the OPC UA Client Driver configuration include a certificate grid. It is important that you understand this tool before proceeding with configuration of the client driver. In particular, take time to review the information in the topic Certificate Name Description.
A certificate grid displays the collection of certificates in a certificate store (which store depends on which grid is displayed) and a set of action buttons.
Certificate Name
The leftmost grid column shows the "Friendly Name" of the certificate, if it has one, and the "Common Name" of the certificate if it does not. Details follow in Certificate Name Description.
Issuer Name
Shows the issuer of the certificate. Self-signed certificates often have the same name as the certificate Common Name, while certificates issued by a Certificate Authority (whether in-house or external) bear the issuer’s name.
Valid
Indicates whether the certificate is valid for the purpose intended. This means slightly different things on different grids.
On the Connection tab or Client Certificate tab, a certificate is considered valid if it still within its validity period. Certificates in the same certificate store that are inappropriate for use are not displayed. Although a certificate might not be marked as valid, it may still be allowed for use by the server or client.
Note that on the Server Certificate tab, the Valid column means that the certificate is within its validity period and the name on the certificate matches the name of the server supplied on the Connection tab Endpoint URL field. This helps you spot if the server responding to the configured Endpoint URL holds a valid certificate for that server.
Thumbprint
The rightmost column displays the SHA-1 "thumbprint" of the certificate. This is the same thumbprint as is shown in the Windows’ certificate dialog displayed by double-clicking a certificate file. This allows identification of certificates that may appear similar in the certificate grid.
Control buttons
The "Create New" button will generate a self-signed certificate and place it in the store being displayed on the certificate grid. Self-signed certificates won't be trusted by other hosts unless the certificate is manually "trusted", which is typically done using the UA server configuration tools.
Click this button to display the following dialog, the content of which will be incorporated in the new certificate.
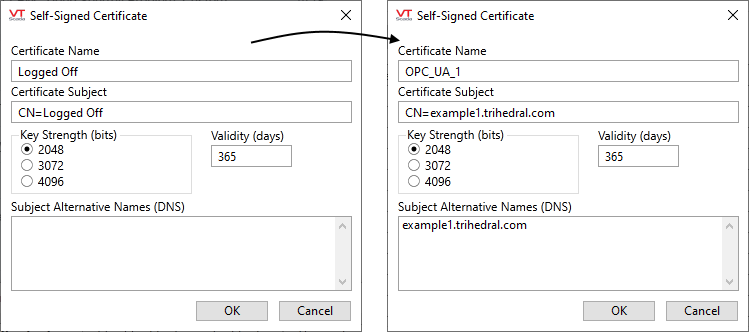
The certificate name is the "Friendly Name" of the certificate. After a certificate is created, the Common Name (CN) cannot be changed, but the Friendly Name can using the Microsoft Management Console (MMC).
The Friendly Name is what the OPC UA Client Driver holds as a parameter to its tag and therefore, is propagated across computers participating in the distributed application.
Previously, if the ClientCertificateName parameter had a value it was not possible to create a new client transport certificate with a different name. Now (12.1.53+), even if the ClientCertificateName parameter has a value, you can create a new client transport certificate with a new name.
Consider the case of a pair of I/O servers (primary and backup). Normally, the primary will connect to the OPC UA server and retrieve data. To do this (assuming the driver is not running in unsecured mode) it needs to provide a Client Certificate to the server. It uses its "ClientCertificateName" tag parameter to find the certificate it should supply. As the backup I/O server contains an exact copy of the tag, it too has the same tag parameter and will therefore look for a certificate of that name in its certificate store.
There is no issue if you install the same certificate (and private key) on both I/O servers. However, you can use different certificates so long as they have the same Friendly Name, as this is the key used by the OPC UA Client to locate its transport certificate. If using secure communication to the OPC UA server, the server must trust both client certificates. This normally requires a manual intervention at your OPC UA server.
You will also have to trust the server certificate on the VTScada client / backup server. See OPC UA Client Driver properties Server Certificate tab. in this topic.
You must create/update certificates with the same names on all backup machines. If you modify ClientCertificateName on your primary you must also ensure that your backup machines have a matching certificate.
Certificate Subject
The certificate subject should be modified. It is the Distinguished Name of the certificate and defaults to "CN=<driver name>", setting the Common Name to the name of the driver tag.
It is advisable to change the certificate subject to the fully qualified domain name (FQDN) of the local machine, to make certificate identification on your OPC UA server easier. If you use the same certificate for you backup machines then choose a meaningful subject name to allow you to identify the certificate on your OPC UA server.
Key Strength
This allows you to set the key strength (number of bits) in the asymmetric key pair that will be generated for this certificate. Currently, the dialog only permits RSA keys (that is all the current OPC UA servers support) of key strengths between 2048 and 4096 bits.
The client and server certificates can have different key strengths.
VTScada will only generate RSA public/private key pairs that are classed as acceptable by:
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-131Ar2.pdf
This mandates at least "112 bits of security", which means an RSA key length of at least 2048 bits.
Referring to Table 4 within the following document, this is sufficient up to the year 2030.
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-57pt1r4.pdf
Validity
The key validity period can be set to be between 30 and 36500 days (approximately one month to 10 years).
When a certificate expires, any entity receiving that certificate should decline it. A shorter validity period may seem inconvenient, but this reduces the length of time that a compromised or stolen certificate remains undetected.
VTScada will raise an alarm when a certificate is within 30 days of expiry to give you time to install newer certificates.
Subject Alternative Names (SAN)
Supply any DNS (Domain Name Service) names that the client computer may be known by. These will be incorporated into the certificate extended properties Subject Alternative Name field as DNS entries. Enter only the DNS values, excluding prefixes. For example, entering "host.example.com" will result in a SAN entry of "DNS Name=host.example.com".
The certificate will also have an automatically-created URL and a DNS entry. The URL is composed from the application GUID and is unique to this application. The DNS entry contains the host name of the workstation on which you are creating this certificate. (Not the fully qualified domain name, FQDN.)
Some OPC UA servers may require that one of the DNS names provided can be matched to a white list, therefore this field gives you an opportunity to provide whatever DNS name is required. The FQDN, as provided in the Certificate Subject, should be included.
Enter each Subject Alternative Name (DNS) on a separate line.
Use Selected button
Enabled only when there are two ore more certificates to choose from.
Use to import a certificate and private key from a Personal Information Exchange format file (.PFX or .P12). This file format is commonly used to securely transport certificates and private keys between computers.
The Microsoft Management Console’s Certificate Management snap-in is one way to export certificates and their private key to such files.
On clicking the button, the following dialog is displayed, which allows you to select the file and supply the password associated with the private key (which is encrypted within the file).
Removes the currently selected certificate (and its private key) from the grid and the associated certificate store.
After removal, a certificate can be restored only if you have a backup of that certificate in a suitable format (e.g. a .PFX or .P12 file). Confirmation is required before the certificate is deleted.
OPC UA Addressing - I/O address formats.
Communication Driver Log-Enabled Variables - Log Enabled Variables.
The ID tab of every tag includes the same common elements: Name, Area, Description, and Help ID.
Name:
Uniquely identifies each tag in the application. If the tag is a child of another, the parent names will be displayed in a separate area before the name field.
You may right-click on the tag's name to add or remove a conditional start expression.
Area
The area field is used to group similar tags together. By defining an area, you make it possible to:
- Filter for particular tag groups when searching in the tag browser
- Link dial-out alarm rosters to Alarm tags having a particular area
- Limit the number of tags loaded upon startup.
- Filter the alarm display to show only certain areas.
- Filter tag selection by area when building reports
When working with Parent-Child tag structures, the area property of all child tags will automatically match the configured area of a parent. Naturally, you can change any tag's area as required. In the case of a child tag, the field background will turn yellow to indicate that you have applied an override. (Orange in the case of user-defined types. Refer to Configuration Field Colors)
To use the area field effectively, you might consider setting the same Area for each I/O driver and its related I/O tags to group all the tags representing the equipment processes installed at each I/O device. You might also consider naming the Area property for the physical location of the tag (i.e. a station or name of a landmark near the location of the I/O device). For serial port or Roster tags, you might configure the Area property according to the purpose of each tag, such as System or Communications.
You may define as many areas as you wish and you may leave the area blank for some tags (note that for Modem tags that are to be used with the Alarm Notification System, it is actually required that the area field be left blank).
To define a new area, type the name in the field. It will immediately be added. To use an existing area, use the drop-down list feature. Re-typing an existing area name is not recommended since a typo or misspelling will result in a second area being created.
There is no tool to remove an area name from VTScada since such a tool is unnecessary. An area definition will exist as long as any tag uses it and will stop existing when no tag uses it (following the next re-start).
Description
Tag names tend to be brief. The description field provides a way to give each tag a human-friendly note describing its purpose. While not mandatory, the description is highly recommended.
Tag descriptions are displayed in the tag browser, in the list of tags to be selected for a report and also on-screen when the operator holds the pointer over the tag’s widget. For installations that use the Alarm Notification System, the description will be spoken when identifying the tag that caused the alarm.
The description field will store up to 65,500 characters, but this will exceed the practical limits of what can be displayed on-screen.
This note is relevant only to those with a multilingual user interface:
When editing any textual parameter (description, area, engineering units...) always work in the phrase editor. Any changes made directly to the textual parameter will result in a new phrase being created rather than the existing phrase being changed.
In a unilingual application this makes no difference, but in a multilingual application it is regarded as poor practice.
Help Search Key
Used only by those who have created their own CHM-format context sensitive help files to accompany their application.
Server List
Select (or create) a named server list.
OPC UA Client Driver properties Connection tab
Use this tab to supply the address of the server.
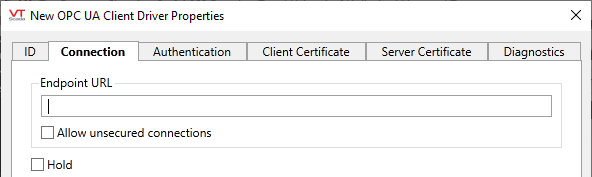
Endpoint URL
The address of a server using the OPC UA binary encoding is known as an Endpoint URL and is expressed as:
opc.tcp://server:port/path
(see: Server Addressing in the topic, OPC UA Addressing)
Select the type of transport security to be used between the VTScada OPC UA Client driver and the OPC UA server.
Enforce Secure Connection
Always connect using the most secure endpoint available (excludes None).
Prefer Secure Connection
Connect using the most secure endpoint available but allow fallback to None as a last resort.
Use Unsecure Connection
Strictly connect using the "None" security policy. If unavailable, the connection will fail.
The "None" security policy permits communication without encryption or message signing (no confidentiality or integrity). This should only be selected for testing or when the connection is otherwise protected by external means, such as a VPN between the VTScada system and the OPC UA server.
Where encryption or cryptographic signing of communication is desired (recommended), a trusted certificate is required at both the OPC UA server and the VTScada OPC UA Client driver to verify identity.
Hold
Select this to have I/O tags attached to the driver hold their last value in the event of a communication failure. If not selected, tags will have their value set to invalid on a communication failure.
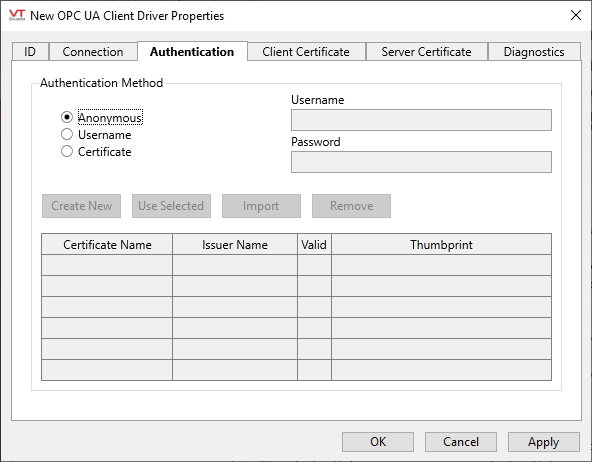
OPC UA Client Driver properties Authentication tab
Refer to OPC UA Support & Security for more detail on required security configuration.
Fields within this tab are enabled according to your selection of authentication method:
Anonymous
When authentication is set to Anonymous, no other fields are enabled.
Username
Username and Password fields are enabled.
Certificate
Control buttons and certificate grid are enabled.
A certificate grid displays the collection of certificates in the current user's Personal Windows certificate store and a set of action buttons. Because a certificate grid appears on more than one tab, it is described at the beginning of this topic rather than within the tab description.
OPC UA Client Driver properties Client Certificate tab
Refer to OPC UA Support & Security for more detail on required security configuration.
Contains a certificate grid and associated buttons, similar to that in the Authentication tab. (See: Certificate Grids and Controls)
Use this to choose the certificate that the OPC UA Client will supply to the server for transport security. It displays only valid certificates of the appropriate extended key usage type (that is, suitable for client authentication) that are in the current user’s Trihedral OPC UA Client certificate store. That certificate store is created by the OPC UA Driver for this purpose.
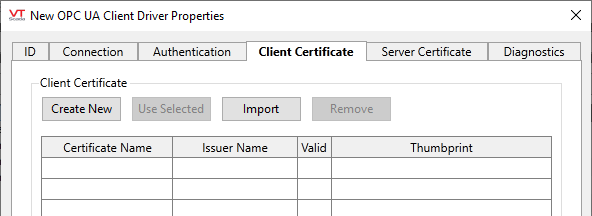
OPC UA Client Driver properties Server Certificate tab
Refer to OPC UA Support & Security for more detail on required security configuration.
This tab holds a pair of certificate grids showing trusted and untrusted server-supplied transport security certificates, if any. (See: Certificate Grids and Controls) The certificates displayed are those in the current user’s Trihedral OPC UA Trusted and Trihedral OPC UA Untrusted certificate stores.
The server provides its certificate during establishment of a connection with the client. The OPC UA Client will only allow the connection to be established if the certificate is trusted.
If the server’s certificate is derived from a trusted certificate authority (in other words, there is a complete chain of trust from the server’s certificate through any intermediate certificates to the trusted certificate authority’s certificate), the certificate will be automatically trusted and not placed in either of these stores.
If the server certificate is not trusted by virtue of such a chain of trust and is not in the Trihedral OPC UA Trusted certificate store, it is automatically placed in the Trihedral OPC UA Untrusted store and appears in this tab’s Untrusted Certificates grid. From there you can elect to trust that certificate, using the Add Trust button. This will remove the certificate from the Untrusted Certificates and place it in the Trusted Certificates grid (and corresponding store).
If the OPC UA Client trusts the server’s transport certificate, via either of the above two methods, then the OPC UA Client will allow a connection to the server to be established.
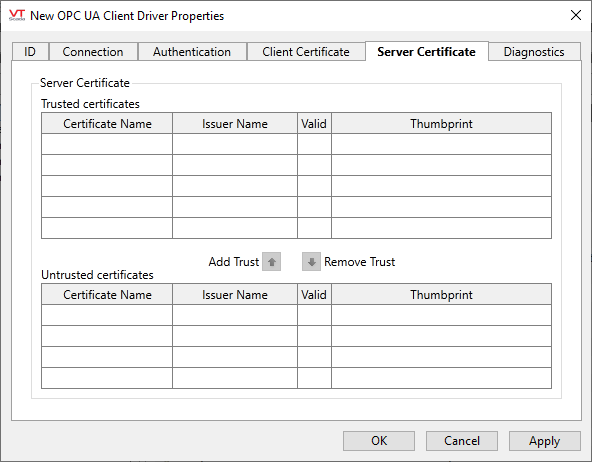
OPC UA Client Driver properties Diagnostics tab
On startup, the OPC UA Client reads certain status and other information from the server. This tab displays the most recent information and provides a button to allow the data to be refreshed. The data is only available when there is a good connection to the server.
There is also a check box that allows an unsecured, unencrypted transport connection to be made to the server (if the server permits such a connection) for debugging purposes. The state of the check box always reverts to unchecked when the driver is reloaded (typically on restart of the application). After selecting or deselecting the check box, use the Restart Driver button to cause the OPC UA Client to disconnect and reconnect to the server, thereby switching between secure and unsecured communication.
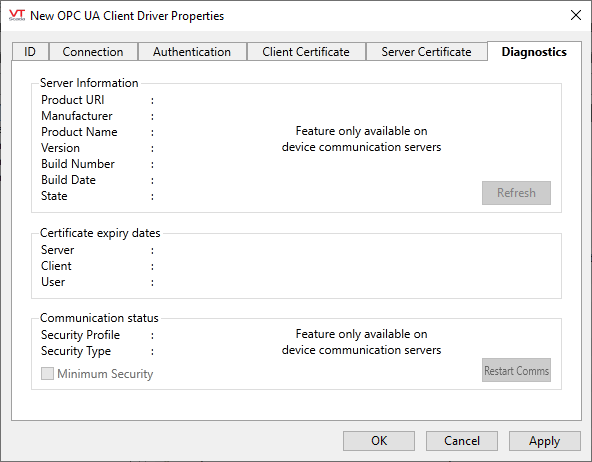
The following widgets are available to display information about your application’s OPC UA Client Driver tags:
Equipment / Status Color Indicator